In this article, we will discuss AWS VPC Virtual Private Cloud. We will go through in detail What is AWS VPC? What is its importance? What are all the key aspects to be considered in this? Also regarding how to use it? So, let’s get started.
AWS VPC
Amazon Virtual Private Cloud (Amazon VPC) is a service that lets you launch AWS resources in a logically isolated virtual network that you define. It is your private network in AWS Public Cloud which allows you to customize your VPC’s network configuration. You have complete control over your virtual networking environment, including a selection of your own IP address range, creation of subnets, and configuration of route tables and network gateways. You can use both IPv4 and IPv6 for most resources in your virtual private cloud, helping to ensure secure and easy access to resources and applications.
By default, AWS provides VPC in every account but this VPC is not recommended for deploying customer environment.
So, what are the components of AWS VPC? What are the mandatory services inside it? What all to be used to make sure your environment is highly secure?
Components of VPC
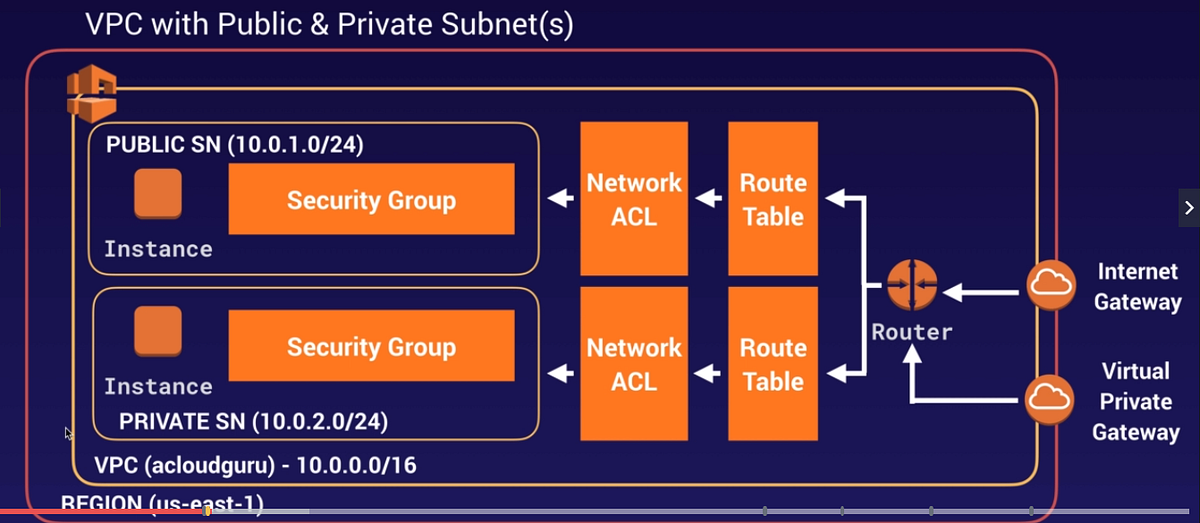
Let’s dive inside VPC now by briefing each component as seen in the above picture. We are moving from outside to inside.
-
Internet Gateway
An internet gateway is a horizontally scaled, redundant, and highly available VPC component that allows communication between your VPC and the internet. IGW is a target for internet-bound traffic from your VPC Route Table, IGW performs network address translation (NAT) for instances that have been assigned public IPv4 addresses.
-
Route Table
A Route Table contains a set of rules, called routes, that are used to determine where network traffic from your subnet or gateway is directed. We see two types of Route Tables one is Main Route Table that automatically comes when you create VPC and another is Custom Route Table that you create for your VPC. Main Route Table controls the routing for all subnets that are not explicitly associated with any other route table.
-
Network ACL
Network Access Control List is a secondary layer of security for your VPC that acts as a firewall for controlling traffic in and out of one or more subnets. Default NACL allows all inbound and outbound IPv4 traffic and, if applicable, IPv6 traffic. You can create a custom network ACL and associate it with a subnet. By default, each custom network ACL denies all inbound and outbound traffic until you add rules.
-
Subnet
AWS VPC Subnet is a division of your entire VPC. When you create a VPC, you must specify a range of IPv4 addresses for the VPC in the form of a Classless Inter-Domain Routing (CIDR) block; for example,
10.0.0.0/16. This is the primary CIDR block for your VPC. After creating a VPC, you can add one or more subnets in each Availability Zone. In the below diagram VPC of 10.0.0.0/16 is divided into multiple subnets across different Availability Zones.
Subnets are of two types Public and Private. In Public Subnet instances are allowed to send traffic directly to the internet via route table. In Private Subnet traffic originated from the instances are not allowed directly to the internet instead it will be routed through NAT Gateway.
5. Security Group: A security group acts as a virtual firewall for your instance to control inbound and outbound traffic. When you launch an instance in a VPC, you can assign up to five security groups to the instance. Security groups act at the instance level, not the subnet level. Therefore, each instance in a subnet in your VPC can be assigned to a different set of security groups.
Below is the path of how traffic moves from inside to outside VPC.
EC2 instance >> Security Group >> NACL >> RouteTable >> Internet Gateway.
Refer to the AWS VPC Official document below.
After looking into basic AWS VPC services such as IGW, RouteTable, Subnet, Security Groups, and NACL in the below first part of the blog let us now continue to look into few other services of VPC.
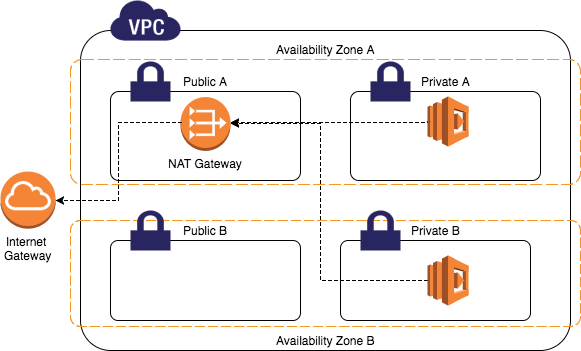
Public and Private instances
Public instances are those which are exposed to the internet and are reachable from the outside world. Public instances are launched in Public Subnet and have Public IP address associated with them.
Private instances are launched in Private Subnet and can not send traffic to the internet directly. Instances in Private Subnet can send traffic via NAT Gateway.
NAT Gateway
Network Address Translation (NAT) gateway that enables instances in a private subnet to connect to the internet or other AWS services but prevents the internet from initiating a connection with those instances. NAT Gateway should always be launched in Public Subent. This service is chargeable at a rate of $0.045 per hour.
Bastion Hosts
These are instances that sit within your public subnet and are typically accessed using SSH or RDP. Once remote connectivity has been established with the bastion host, it then acts as a ‘jump’ server, allowing you to use SSH or RDP to log in to other instances (within private subnets) deeper within your VPC.
Public instances are associated with Public IPv4 addresses and are changed when an instance is started and stopped. If you want to keep the IP address of the Public instance then have to associate the Elastic IP address to it.
Elastic IP
An Elastic IP address is a static IPv4 address designed for dynamic cloud computing. An Elastic IP address is allocated to your AWS account and is yours until you release it. When you associate an Elastic IP address with an instance, it is also associated with the instance’s primary network interface.
Learn more about Elastic IP in the below AWS documentation.
https://docs.aws.amazon.com/AWSEC2/latest/UserGuide/elastic-ip-addresses-eip.html
What are the Stateful and Stateless rules in AWS VPC?
Security Groups are Stateful – When you allow port 80 in the inbound rules for an EC2 instance security group it is automatically allowed to go out via outbound rules through port 80. Hence, Security Groups are called Stateful.
NACL’s are Stateless – Unlike Security groups, you need to explicitly mention both inbound and outbound rules in Network ACL for the traffic to come in and go out on port 80.