Cloud security tools have become pivotal in the realm of cloud computing, offering robust protection for cloud-based infrastructures against intricate cyber threats.
In this blog, we have presented below the top cloud security tools renowned for their proficiency in identifying, evaluating, and mitigating cybersecurity risks.
Let’s dive in!
What are cloud security tools?
Cloud security tools are pivotal in protecting cloud-based systems, infrastructure, and data. It is tailored to find any security challenges the cloud faces, including data loss, data breaches, and account hijacking.
These tools come up with diverse security features such as asset mapping, vulnerability scanning, threat finding and protection, backup and recovery, and much more. It helps to strengthen the security posture and defend against the potential security threats.
According to data from Statista, the expenditure on Cloud IT infrastructure is projected to approach nearly US$ 94 billion in 2023.
While this transition towards cloud-based solutions offers numerous benefits, it also introduces potential challenges. The expanding landscape of cloud computing has inadvertently led to increased data vulnerabilities and associated security concerns.
As advancements in cloud infrastructure continue, so do the emergence of novel cyber threats aimed at compromising its integrity. Statista further highlights that the global market for cloud security software was valued at US$ 29.5 billion in 2020, with expectations to escalate to around US$ 37 billion by 2026.
North America currently dominates the market for cloud security tools, but the Asia Pacific region is witnessing the most rapid growth. The surge in cloud adoption in recent years underscores the urgency for enhanced cloud security measures. In our discussion, we’ll delve into the intricacies of cloud security tools and explore strategies for leveraging cloud threat protection to safeguard your valuable data.
Cloud security tool types
In today’s cloud market, there are numerous cloud-based security tools and technologies available to achieve reliable data protection.
Here we have listed some of the valuable cloud security tools for your organization:
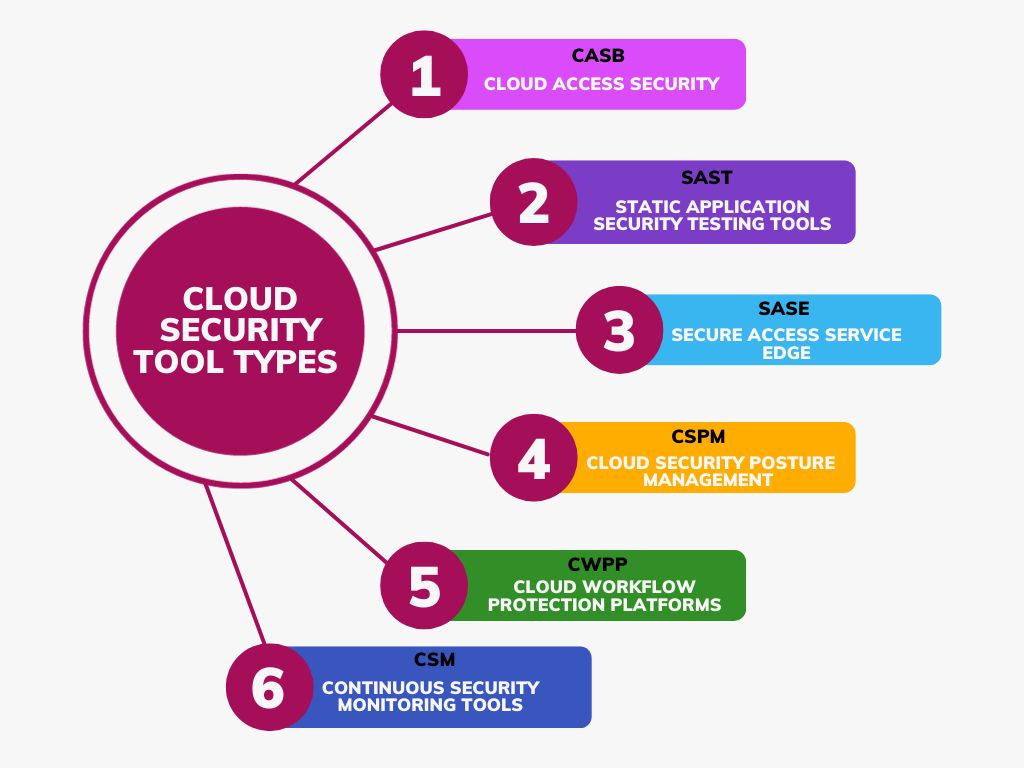
- Cloud Access Security (CASB): It is an on-premise cloud application security tool. If you want to monitor the SaaS application usage, then CSAB will be the best option for you. The varied security policy enforcement types such as single sign-on, encryption, authentication, device profiling, and malware detection can be consolidated with the help of this tool.
- Static Application Security Testing tools (SAST): SAST tools assist in finding security flaws by analyzing the source code. The test coding was carried out in real-time to prevent loss of time and data-related security issues. The prime benefit of utilizing this tool is to monitor and detect well-known security issues such as SQL injection flaws or overflows.
- Secure Access Service Edge (SASE): It is one of the foremost security components in the network architecture and it is otherwise called a secure service edge (SSE) . It integrates VPN and SD-WAN capabilities with firewalls, CASB, Secure web gateways, and zero-trust network access (ZTNA). They offer secured access to the SaaS, the company’s applications, and the web irrespective of the device or location.
- Cloud Security Posture Management (CSPM): This kind of security tool helps to achieve automation in the identification and remediation of the risks across the security management for the varied cloud platforms such as SaaS, PaaS, and IaaS. It also helps in the visualization of the risks, risk assessment, risk remediation, incident response, DevSecOps integrations, and monitoring of compliance.
- Cloud Workflow Protection Platforms (CWPP): These platforms offer seamless cloud security solutions with minimal disruption. Tailored for the fast-paced DevOps environment, they efficiently identify tasks operating across various cloud settings.
- Continuous Security Monitoring Tools (CSM): For real-time threat detection and continuous configuration, you can opt for this tool. They aggregate and analyze the data for monitoring suspicious activity from varied origins such as system event logs, user activity, and network traffic. Whenever the threat is detected, the notification will be passed to the DevSec Team.
Top 10 Cloud Security Tools for 2024
Recent developments, including the rise of remote work and the emergence of cloud-native applications, have underscored the significance of cloud security tools within the cybersecurity domain. These tools are essential in providing immediate insight into potential risks that organizations may encounter across a dispersed network encompassing applications, users, and infrastructure.
Additionally, a unified dashboard that consolidates an organization’s assets is a hallmark feature of contemporary cloud security solutions.
While many cloud security platforms offer fundamental features like web application firewalls (WAFs), oversight of misconfigurations, API security, access management, user authentication, automation, and identity access management (IAM), the market is brimming with advanced solutions.
Below, we’ve curated a selection of top-tier tools currently available on the market, presented in no specific sequence, designed to fortify your systems against cyber threats, data breaches, and significant penalties.
Here are a few promising and pocket-friendly security tools that can be installed in your organization:
Microsoft Azure Security Center
The Microsoft Azure Security Center serves as a cloud-based tool tailored for the monitoring of security within Azure environments. This system harnesses the capabilities of behavioral analytics coupled with machine learning to swiftly identify and address security threats.
Beyond mere detection, it also offers evaluations of vulnerabilities and provides actionable recommendations to fortify the security infrastructure.
Azure Security Center doesn’t just stop at identification; it actively enforces robust security policies to shield assets within Azure. To ensure users get the most out of this platform, Microsoft extends its support through an array of resources such as comprehensive documentation, active community forums, and an around-the-clock dedicated support center.
Google Cloud Security Command Center
Designed with a holistic approach, the Google Cloud Security Command Center presents businesses with an integrated platform to manage and oversee their security posture across the Google Cloud ecosystem.
It stands out with its cutting-edge threat detection capabilities, empowering organizations with immediate analytics and insights into their cloud environment’s security. This platform acts as a sentinel, offering a unified perspective of security protocols and ensuring consistent security management.
For users navigating the platform, Google provides an extensive knowledge base, community-driven discussions, and a support hub that encompasses a variety of service offerings.
Cisco Cloudlock
Positioned as an avant-garde solution for the evolving cloud landscape, Cisco Cloudlock is purpose-built for the unique demands of cloud-native operations. Its comprehensive suite of security functionalities addresses various aspects, from safeguarding critical data to offering deep threat intelligence insights.
Notably, its significance shines in enhancing security for Software-as-a-Service (SaaS) applications, underscoring the importance of tailored solutions in today’s cloud-centric world.
Organizations that integrate Cisco Cloudlock into their infrastructure benefit from fortified data security measures, proactive breach mitigation strategies, and unwavering adherence to cloud-specific security benchmarks.
Palo Alto Networks Prisma Cloud
Palo Alto Networks’ Prisma Cloud emerges as a formidable Cloud Security platform designed to a diverse range of needs spanning workload protection, containerized applications security, compliance oversight, and threat intelligence.
Its integrated approach streamlines cloud security, ensuring transparency, adherence to compliance mandates, and robust protection across various cloud providers. The platform’s strength lies in its expansive set of security protocols, covering every facet from container integrity to real-time threat prevention.
Ensuring users are equipped to maximize their potential, Palo Alto Networks extends its support through dedicated customer portals, comprehensive knowledge repositories, and a team of seasoned security experts.
Trend Micro Cloud One
At the forefront of comprehensive cloud security solutions stands Trend Micro Cloud One, designed to address the multifaceted challenges presented by cloud environments. Its offerings encompass a broad spectrum, from safeguarding workloads to intricate file integrity monitoring and container security.
By leveraging its sophisticated threat intelligence mechanisms, organizations can elevate their security stance, effectively thwarting emerging threats. As users navigate its offerings, Trend Micro ensures a seamless experience with robust technical support, an intuitive customer portal, and a wealth of knowledge at their fingertips.
Cloudflare Cloud Security Solutions
Cloudflare’s cloud security suite is engineered to safeguard web-centric assets, offering a comprehensive suite that spans DDoS mitigation, web application firewalling, and content delivery optimization.
By harnessing the expansive reach of Cloudflare’s global network, organizations can bolster the security, performance, and accessibility of their cloud-based applications. Emphasizing security, Cloudflare integrates robust protocols such as SSL/TLS encryption, DNSSEC, and advanced DDoS protection mechanisms.
Ensuring users remain supported and informed, Cloudflare provides 24/7 assistance through diverse channels and an expansive repository of documentation and community forums.
Qualys Cloud Platform
The Qualys Cloud Platform stands as a beacon for organizations navigating the complexities of cloud security and compliance. Its cloud-native architecture delivers a suite of tools focused on vulnerability management, continuous monitoring, and rigorous compliance assessments.
Through its offerings, organizations gain the ability to preemptively identify vulnerabilities, evaluate associated risks, and uphold stringent compliance standards. Qualys ensures users receive unparalleled support, offering multiple channels for technical assistance, in-depth training modules, and certification programs to augment user proficiency.
Check Point CloudGuard
Check Point CloudGuard emerges as a comprehensive cloud security suite, adeptly addressing the nuanced requirements of both public and private cloud environments.
With a focus on advanced threat prevention, network security, and cohesive security management, CloudGuard seamlessly integrates with leading cloud platforms, ensuring holistic protection against sophisticated cyber threats.
Its comprehensive security offerings span firewall capabilities, intrusion prevention systems, and proactive threat prevention mechanisms. To facilitate a seamless user experience, Check Point extends its support through a user-centric portal, exhaustive documentation, and a responsive support team.
IBM Cloud Pak for Security
IBM’s Cloud Pak for Security represents a fusion of advanced security functionalities, seamlessly integrating threat intelligence, analytics, and automation. This holistic platform empowers organizations to detect, analyze, and respond to security incidents across varied cloud and hybrid environments.
By using capabilities of advanced analytics and AI-driven insights, IBM Cloud Pak for Security ensures organizations remain a step ahead, proactively identifying and mitigating potential threats. To fortify its users’ experiences, IBM offers a diverse range of support channels, ensuring prompt assistance and guidance on platform-related queries.
Cloud Security Best Practices
Effective cloud security hinges on a combination of proactive measures and continuous vigilance.
Prioritizing robust authentication mechanisms, ensuring timely software updates, encrypting sensitive data, maintaining an ever-watchful eye on security metrics, and fostering a culture of security awareness through regular training is paramount. These practices, when diligently implemented, create a robust security framework, safeguarding organizational assets in the cloud.
Conclusion
As the digital landscape becomes increasingly adopting cloud technologies, organizations must remain vigilant, adapting to emerging threats and leveraging cutting-edge solutions.
The coming years promise a confluence of advancements, driving the evolution of cloud security services, and ensuring organizations remain resilient and secure amidst evolving cyber landscapes.
For optimal cloud security, enterprises should combine these tools with best cloud security practices like robust authentication, regular updates, encryption, vigilant monitoring, and continuous employee training.