Many organizations migrating to the cloud platform for critical workload management, but the real concern is securing that workload. The best solution for it will be the adoption of a well-defined risk management strategy, which can assure security to the infrastructure and application layer, with the usage of security control.
Microsoft assumes responsibility for safeguarding the Azure platform, while customers are tasked with utilizing a variety of security tools and features to ensure the security of their applications, infrastructure, and cloud environment.
Typically, customers will need to combine native Azure tools with third-party services to address any potential security gaps. In this blog post, we will delve into cloud-native security tools and services within Azure that can be employed to implement essential security controls.
Let’s dig in!
What is Azure security?
Azure security means security tools and features available on the Azure cloud platform. Azure supports multiple programming languages, frameworks, devices, operating systems, and so on. The customers can access the Azure service as well as resources whenever it gets connected to the internet.
In Gartner’s 2021 Magic Quadrant for Cloud Infrastructure and Platform Services, Microsoft Azure, along with Google and AWS, stands out as one of the top three leaders. The Cloud Shared Responsibility Model places the responsibility for securing infrastructure, applications, data, and identities squarely on the shoulders of every customer transitioning to the cloud.
Microsoft Azure steps up to the challenge by offering native security tools like Microsoft Cloud Defender, effectively fortifying cloud environments against emerging threats. Additionally, Microsoft Azure collaborates with third-party security services to provide advanced security capabilities, often complementing the robust set of native Azure tools available.
The Microsoft Azure cloud Security infrastructure works as a shared security responsibility model, which means the security can be shared effort between the customers and Azure in the cloud platform, except the on-premise network. However, when the customers moved into the cloud, the security responsibilities of Azure also transferred.
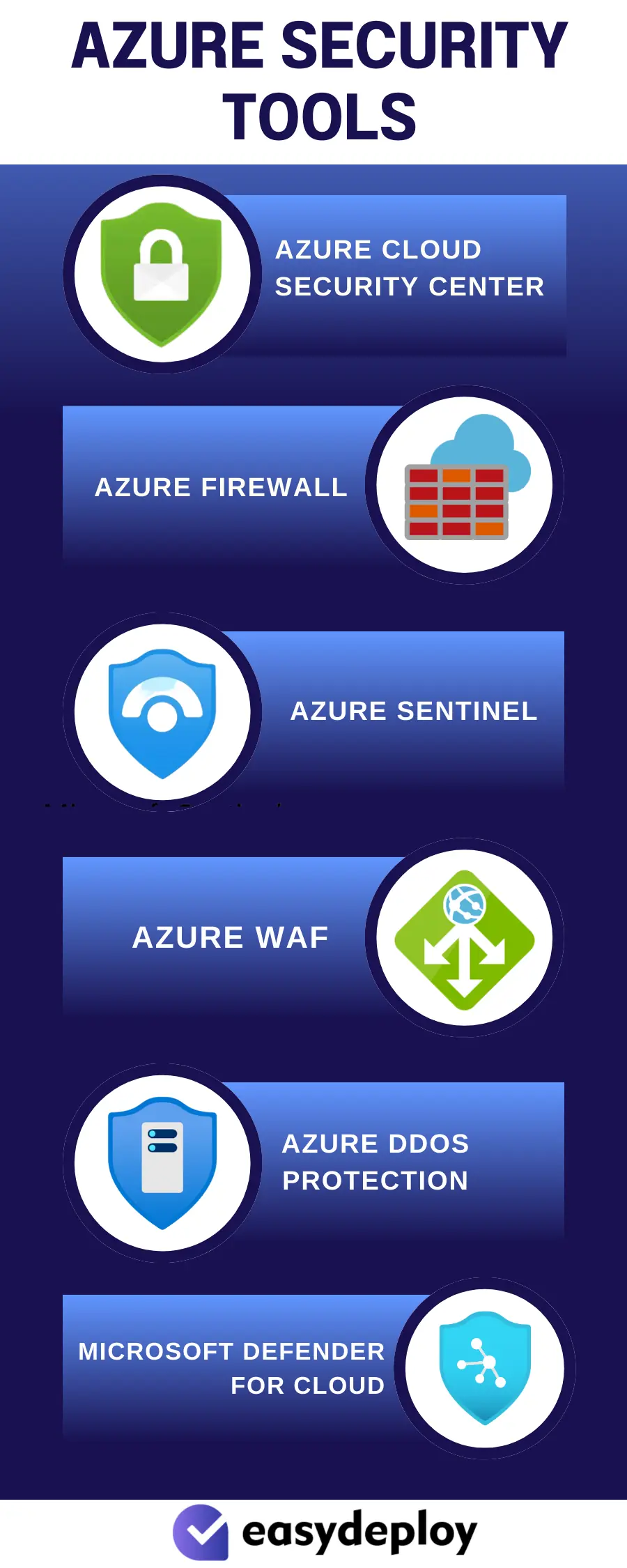
Azure Security Tools and Features
Here are some Azure security tools and features that can be utilized to ensure the security of the workloads:
-
Azure Cloud Security Center
Azure Security Center is the native cloud-based security posture management Azure cloud security service. The infrastructure management for the workloads in the Azure cloud as well as on-remises carried out in a centralized way. The workload deployments that occur will be monitored periodically against pre-defined best security practices and misconfigurations that occurred for the remediation.
Azure cloud security center speeds up the threat detection and remediation process in the Azure cloud environment.
Azure security center validates the security posture using a secure score achieved for the subscribed resources and aids the end users to prior the task remediation process to level up the score. Those remediation activities will be done from the security center itself and others need human resources involvement for getting the remediation guidance.
Azure cloud security center has some integrated features as listed below:
- Adaptive application controls: It defines the set of safe applications to defend the malicious software that runs on the cloud resources and also it generates security alerts to enable threat protection activities.
- Azure Defender: Azure security center also comes up with additional features such as a vulnerability assessment option known as Azure Defender. For achieving high security, enabling vulnerability assessment and reporting options is of paramount importance.
- Security posture management: It is generally preferred when you are doing activities in heterogeneous multi-cloud environments. It suggests cyber risk-based remediation solutions to combat cyber threats and risks.
2. Azure Firewall
Azure firewall, is a highly manageable, stateful firewall service intended mainly for Azure workloads that are integrated into VNet. It can be adopted across highly available zones and can support highly scalable traffic in the cloud.
It functions by setting the central configuration rules in the various networks and subscriptions to allow only authorized traffic.
The threat intelligence capability of Azure firewall can protect the workloads from the high traffic evolves from malicious domains and internet protocols. From the threat intelligence feed, the Azure firewall receives data about the traffic rate. It also comes up with an option such as FQDN filtering for restricting the external traffic networks.
3. Azure Sentinel
Azure Sentinel is one of the powerful native cloud SIEM tools and it infuses the capabilities of SIEM and SOAR solutions. It can be able to detect and respond to threats and attacks as it has the in-built AI. Threat monitoring can be made in the ecosystem such as cloud to on-premises, workstation, and personal devices.
Azure sentinel acts as a central repository for the threat intelligence and telemetry data. For instance, customers can utilize the AWS cloud connector for streaming the data from the AWS CloudTrail into Azure sentinel. Azure Sentinel also has security orchestration and automated response capabilities. The customers can make use of those capabilities to enable automation rules and playbooks to respond to the threats that are identified.
The playbooks used were completely based upon the Azure logic applications and used for triggering workflows defined once the threat has been detected. Furthermore, it has built-in hunting queries for detecting anomalies in the data logger. To tailor the threat detection activities, security analysts can create customized queries in the Azure portal.
4. Azure Web Application Firewall (WAF)
Azure Web Application Firewall (WAF) is a robust security solution designed to safeguard web applications against a multitude of known vulnerabilities. It offers a centralized defense mechanism that can detect and protect against vulnerabilities that might have slipped through the cracks during the development phase.
This means that any known threats, whether they are new or existing, are promptly addressed and updated at the WAF level before malicious actors can exploit them. This not only enhances security but also reduces the administrative burden of having to mitigate vulnerabilities for each application.
The preconfigured WAF rules are highly effective at shielding business applications from various attack patterns, including SQL injection, cross-site scripting (XSS), PHP injection, and remote command execution. Azure WAF can be easily enabled in conjunction with popular Azure frontend services such as Application Gateway, Azure Front Door, and CDN (currently in preview).
WAF for Application Gateway is powered by the OWASP ModSecurity Core Rule Set and is continuously updated to protect against newly identified vulnerabilities, all without requiring manual intervention.
5. Azure DDoS Protection
Azure provides continuous DDoS (Distributed Denial of Service) Protection for all workloads hosted on its platform. While basic protection is automatically enabled, customers also have the option to choose the DDoS Protection Standard for more advanced defense against DDoS attacks.
DDoS Protection Standard includes several additional features such as logging, telemetry, alerting, mitigation reports, and cost protection.
DDoS Protection Standard seamlessly integrates with and offers ready-made protection for workloads deployed within an Azure Virtual Network (VNet). It safeguards your workloads against both Layer 3 and Layer 4 attacks, and when combined with Azure Web Application Firewall, it extends protection to Layer 7, which focuses on application-level security.
Furthermore, this service provides comprehensive reports on attack analytics, allowing you to gain deeper insights into the types and characteristics of attacks. Azure DDoS Protection is highly effective at mitigating a wide range of attacks, with the ability to detect and counteract as many as 60 different attack types at scale.
6. Microsoft Defender for Cloud
Defender for Cloud is a cloud security posture management (CSPM) tool and it is mainly used for detecting cloud vulnerabilities and helping businesses to handle evolving threats. This tool also helps to take effective security issues from a central network, which significantly saves time and effort.
Microsoft Defender for Cloud has the capabilities such as:
- A development security operations DevSecOps solution that helps to manage the security at the code level across the multi-cloud and multiple pipeline environments
- A cloud security posture management (CSPM) solution that helps to prevent breaches by taking effective actions
- A cloud workload protection platform (CWPP) with defined protections for containers, servers, databases, storage, and other workloads
Thus enabling Azure security services, you can secure the workloads available on the Azure cloud platform.
Azure Cloud security controls
Azure categorizes its security tools into various segments, including operations, applications, storage, networking, and computing. Identity management has become a critical concern for enterprises in the cloud, and Azure offers a range of core identity management functions:
- Multi-factor authentication: Azure enforces the use of multiple identity verification methods, enhancing account security. It also supports single sign-on to streamline identity and password management.
- Continuous monitoring: Azure provides real-time security monitoring, and alerts, and utilizes machine learning for insightful reports. It also includes robust threat detection and remediation capabilities.
- Comprehensive identity management: Azure’s cloud-based Active Directory is an Identity and Access Management (IAM) solution that secures both on-premises and cloud data. It simplifies the management of groups and users while allowing engineers to implement policy-based identity management directly into applications.
- Device management: Azure enables you to establish security measures at the device level. You can manage how both cloud and on-premises devices access your corporate data, ensuring a high level of security.
Azure’s identity management functions play a vital role in strengthening the overall security of your cloud environment, offering a comprehensive set of tools to safeguard your data and resources.
Azure Security Best Practices
You can refer to the Azure Security documentation to know the best security recommendations and best practices. Here are some Azure security best practices for you:
- To utilize the additional features and functionalities such as finding and fixing security threats, detecting threats, and quick response to attacks, you can upgrade your Azure subscription to the Azure security center.
- The keys must be stored in the Azure key vault to secure the passwords, secrets, and database credentials.
- Installation of a web application firewall is advisable
- You can use the Azure multi-factor authentication for securing the admin accounts
- Hard disk files must be encrypted
- You have to connect the Azure virtual machine to the networking devices by placing it on the Azure virtual networks
- Azure DDoS services can be employed to prevent and mitigate attacks
- Must use the security policies to prevent the threats and attacks. The auto-generated security policy can be enabled as per Azure subscription.
- You must review the Azure security center dashboard regularly. With the help of a dashboard, you can view the current status of the Azure resources and take effective actions.
- It is recommended to deploy Azure security center RBAC. There exist five in-built roles and two security roles. The roles vary in the permissions.
Summary
Hope this article covers all the information about Azure security, Azure security tools, Azure security best practices, and so on.
Utilizing the above-mentioned tools is essential for bolstering the security of your Azure cloud workloads, offering protection against a wide range of threats and vulnerabilities.
Easydeploy has a collective of independent software vendors united by a shared mission and helps users enhance their cybersecurity defenses. Discover our cloud data protection solution today and book a demo to see it in action.
FAQ
- How does Azure Web Application Firewall (WAF) contribute to securing web applications on Azure?
Azure WAF is a robust security solution safeguarding web applications against known vulnerabilities, offering centralized defense mechanisms and preconfigured rules for protection against various attack patterns.
2. Why is securing cloud workloads a significant concern for organizations migrating to a cloud platform?
Organizations migrating critical workloads to the cloud face security concerns, making the adoption of a well-defined risk management strategy crucial.