The evolution of Cloud Computing has changed the perspective of how we store and secure our data in the public cloud. While security is a major concern here, the first level of securing and restricting access to data is by implementing AWS Identity and Access Management.
In this blog, we are going to discuss one of the core security and user management services of Amazon Web Services i.e Identity and Access Management (AWS IAM). We will also look at how to create an IAM user and give required access, CLI commands to interact with IAM and Best practices of IAM to getting the full benefits of this service.
As per the official definition, “AWS Identity and Access Management (IAM) is a web service for securely controlling access to AWS services. With IAM, you can centrally manage users, security credentials such as access keys, and permissions that control which AWS resources users and applications can access.”

Using IAM, you can create and manage AWS users and groups, and use permissions to allow and deny their access to AWS resources.
Before we start looking into the console let’s understand key aspects of IAM –
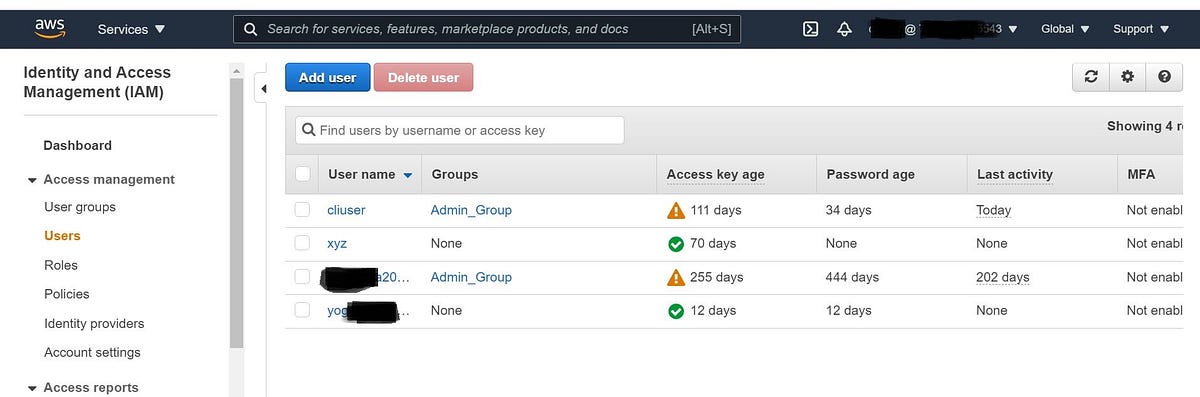
- Users – AWS IAM User is an entity that you create in AWS to represent the person or application that uses it to interact with AWS.
- Roles – An IAM role is an entity with permissions to make AWS service requests. Roles are attached to AWS users say in account A through which they can access another account B or Roles are attached to AWS Services such as EC2 so that they can call (API calls) another service say S3.
- Policies – Roles are to access another account or service whereas, Policies are the permissions associated with a user. When a user tries to perform any action in any other account or service AWS evaluates the attached Policies and determines whether the request is allowed or not.
IAM users can access the AWS resources in two ways:
- Programmatic access – User needs access key ID and secret access key for using the AWS services via AWS API, CLI, SDK, and other development tools.
- AWS Management Console access – Needs a password through which he can access the console and perform tasks as per given rights.
Steps to create an IAM user and give management console access with read-only access:
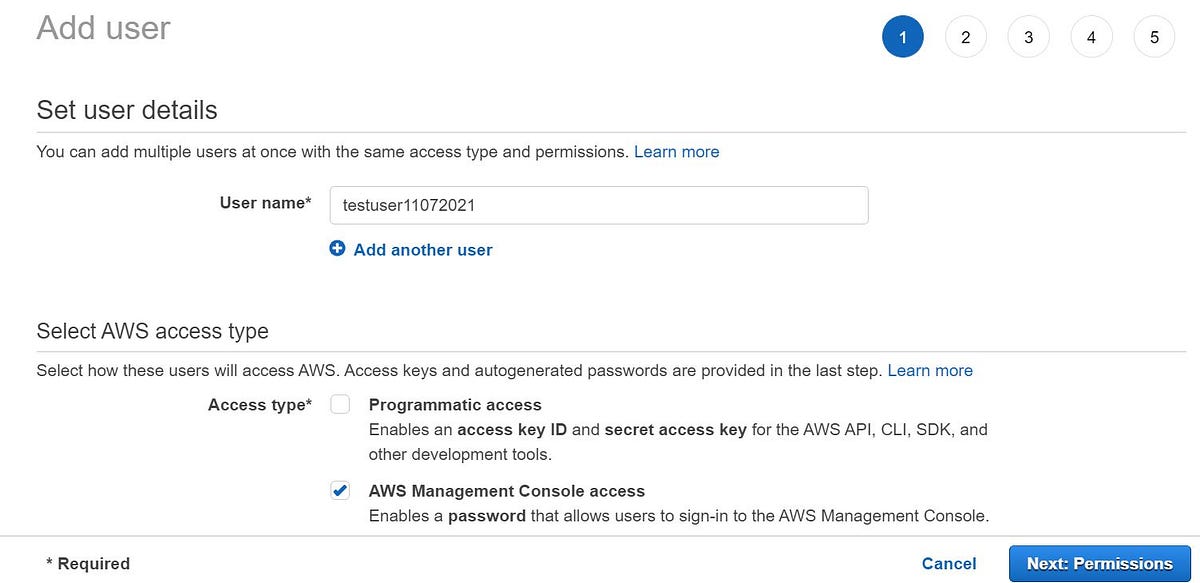
- Log in to your console as a root user (admin of the account) and go to the IAM console. Select User and give the Username and select AWS management console access.
2. Next > Go to the permissions page and click attach existing policies (here we are only focusing on users and policies so not creating any groups) and select ReadonlyAccess.
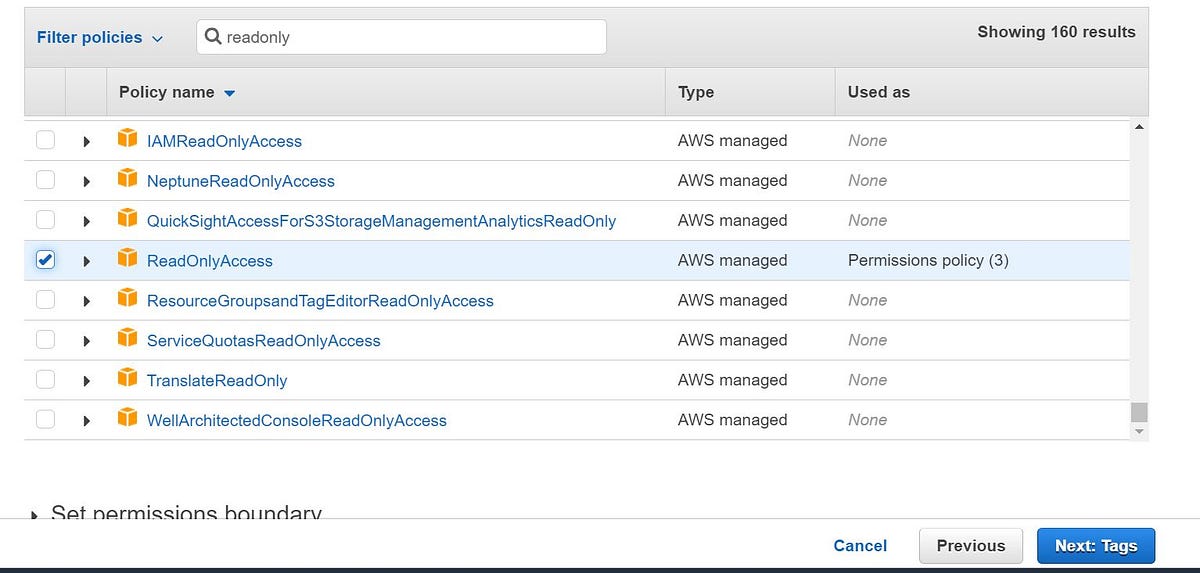
3. Review the details and click Create user. A new user with Read-only access is now created and you need to share the details with him/her in order to access the console and start working.

AWS IAM switch role – Let us consider a scenario where your infosec team member needs to do some security test on each individual accounts and we are supposed to give him read access to these accounts. In this situation, we need to make use of the switch role service and give the necessary account access so the user can perform the required activities.
Moving on, we need to always make sure we adhere to the best practices of AWS IAM and they are listed below:
- Grant least privilege access: Establishing a principle of least privilege ensures that identities are only permitted to perform the most minimal set of functions necessary to fulfill a specific task, while balancing usability and efficiency.
- Use AWS Organizations: Centrally manage and govern your environment as you scale your AWS resources. Easily create new AWS accounts, group accounts to organize your workflows, and apply policies to accounts or groups for governance.
- Enable Identity federation: Manage users and access across multiple services from your preferred identity source. Using AWS Single Sign-On centrally manage access to multiple AWS accounts and provide users with single sign-on access to all their assigned accounts from one place.
- Enable MFA: For extra security, we recommend that you require multi-factor authentication (MFA) for all users.
- Rotate credentials regularly: Change your own passwords and access keys regularly, and make sure that all users in your account do as well.
- Enable IAM Access Analyzer: Enable IAM Access Analyzer to analyze public, cross-account, and cross-organization access.
CLI Commands for AWS IAM:
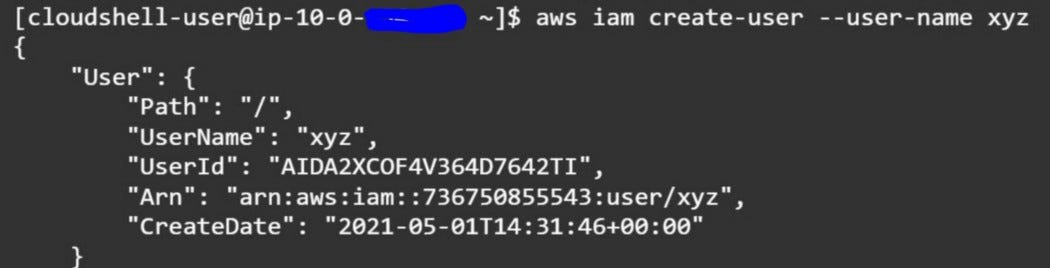
- Create IAM User — “aws iam create-user — user-name xyz”
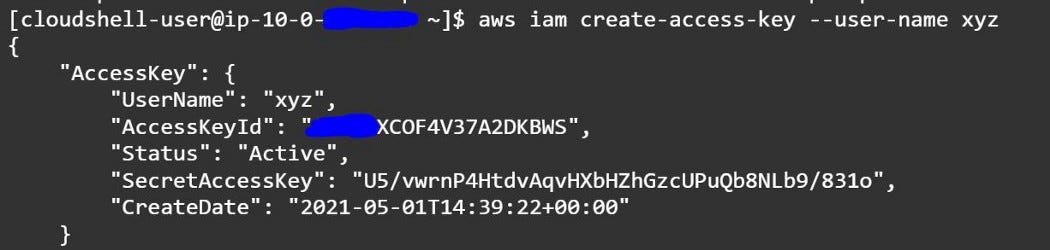
2. Create Access Key- “aws iam create-access-key — user-name xyz”
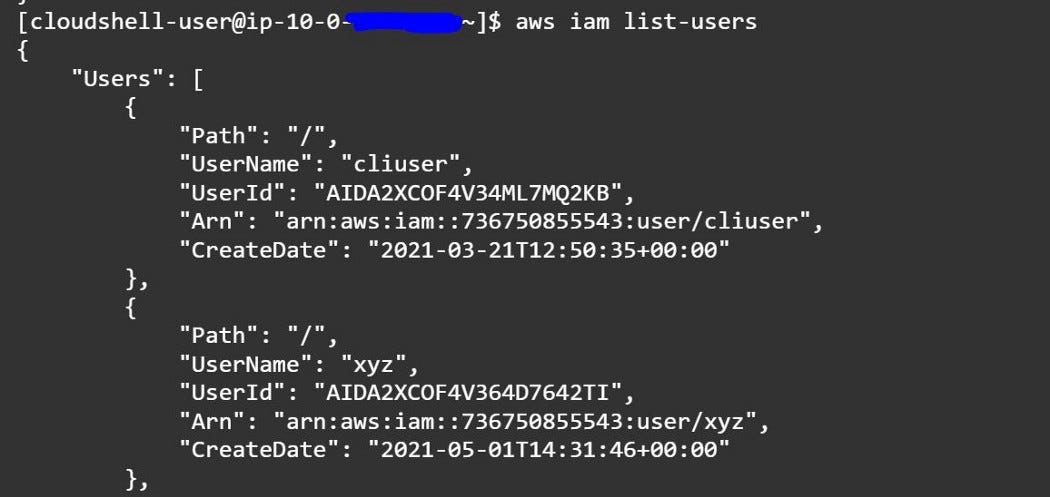
3. List AWS IAM Users — “aws iam list-users”
Please refer to the official documentation on AWS IAM from Amazon in this link “https://docs.aws.amazon.com/iam/”
AWS CLI reference “https://docs.aws.amazon.com/cli/latest/reference/iam/”
AWS IAM FAQ’s –
- Who is able to manage users for an AWS account?
The AWS account holder can manage users, groups, security credentials, and permissions. In addition, you may grant permissions to individual users to place calls to IAM APIs in order to manage other users. For example, an administrator user may be created to manage users for a corporation – a recommended practice. When you grant a user permission to manage other users, they can do this via the IAM APIs, AWS CLI, or IAM console. - What kind of key rotation is supported for IAM users?
User access keys and X.509 certificates can be rotated just as they are for an AWS account’s root access identifiers. You can manage and rotate programmatically a user’s access keys and X.509 certificates via the IAM APIs, AWS CLI, or IAM console.
Look at the more faq’s here at https://aws.amazon.com/iam/faqs/.
IAM is a feature of your AWS account offered at no additional charge. You will be charged only for use of other AWS services by your users.
Let us know more about the Switch role, User Policies, Groups, and other Programmatic access of AWS in our next blogs.
Conclusion
AWS Identity and Access Management must become a mandatory use in your environment. Make the best use of it by fine-grained access control to AWS resources, Multi-factor authentication for highly privileged users, Analyze access and, Integrate it with your corporate directory.
As IAM ensures security and data privacy always make sure you adhere to the best practices of IAM. When all aspects are covered your data is safe, secure, and reliable.