We have seen in detail what is AWS IAM and how to implement it in our previous blog. https://www.easydeploy.io/blog/what-is-aws-identity-and-access-management-iam/
Now, in continuation of it let us discuss what are AWS IAM (Identity and Access Management) Roles and Policies, how to implement them, and make the best use of it to fine grain the permission to your environment.
IAM Roles
An IAM role is an IAM identity that you can create in your account that has specific permissions. These roles define the set of permissions for making AWS service request. IAM roles do not have long-term credentials stored in them instead when you assume a role it provides you with temporary security credentials for your role session.
IAM roles are normally attached to Users or Applications that do not have specific accounts yet they are in need of access to AWS services.
Let us consider an example in which our EC2 machine wants full access to an S3 bucket in order to perform some operations related to files. Here, embedding a security key inside EC2 is not an ideal solution as anybody can crack the keys and gain access to our data on the S3 bucket. Instead, let us make use of attaching an IAM Role to our EC2 machine so it has access to the S3 bucket without hard coding any credentials.
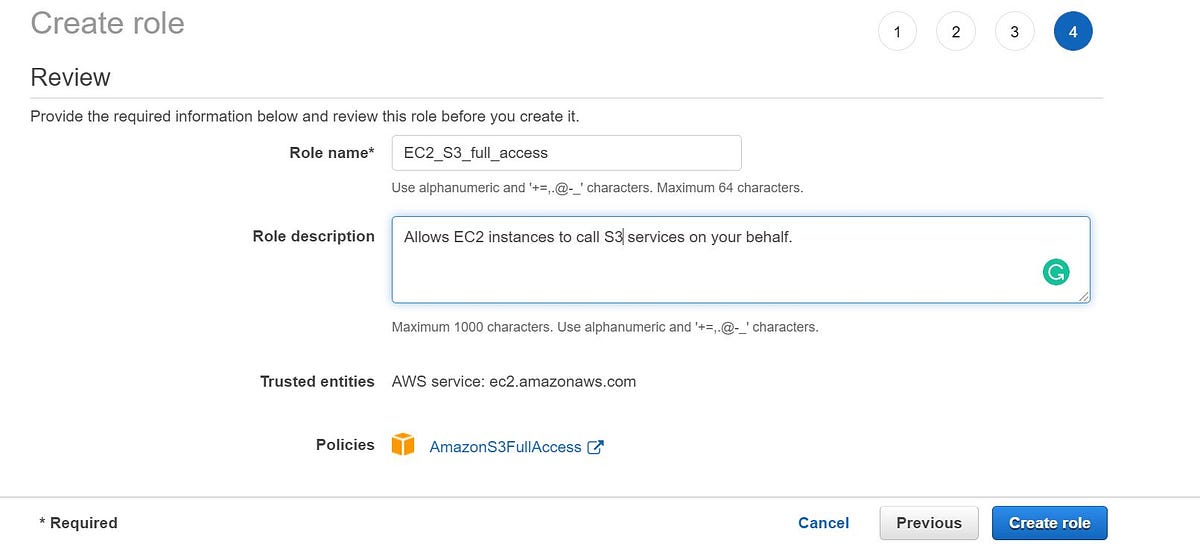
The first part is to create an IAM Role:
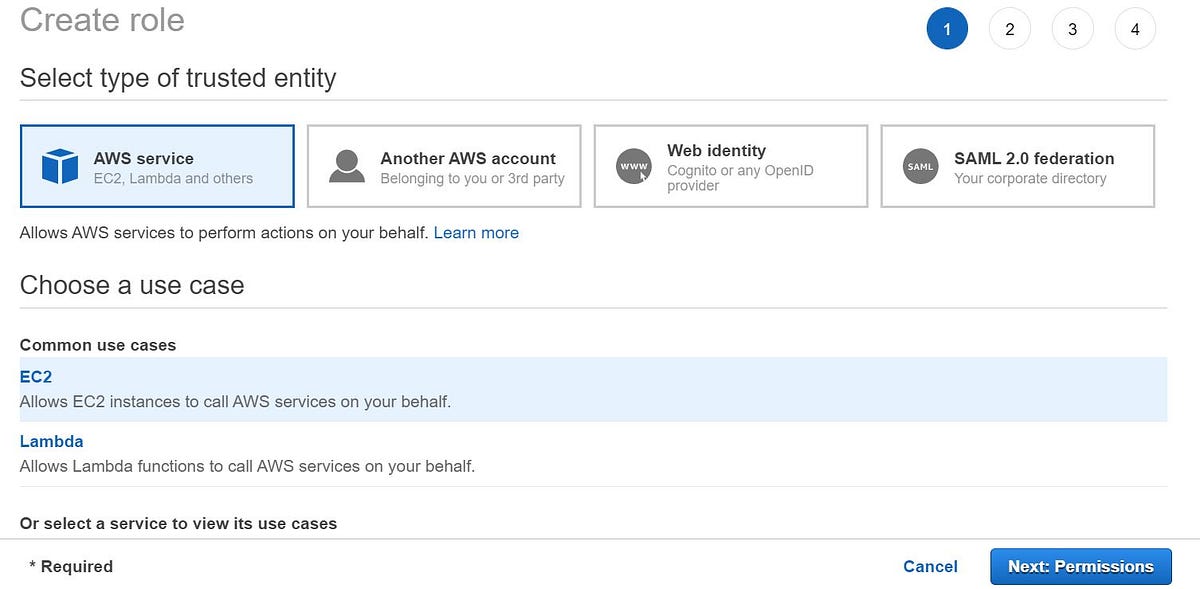
- Under IAM go to Create a role and select AWS service i.e EC2 in this case (you can attach a role to another account, web identity, or also to other corporate federations).
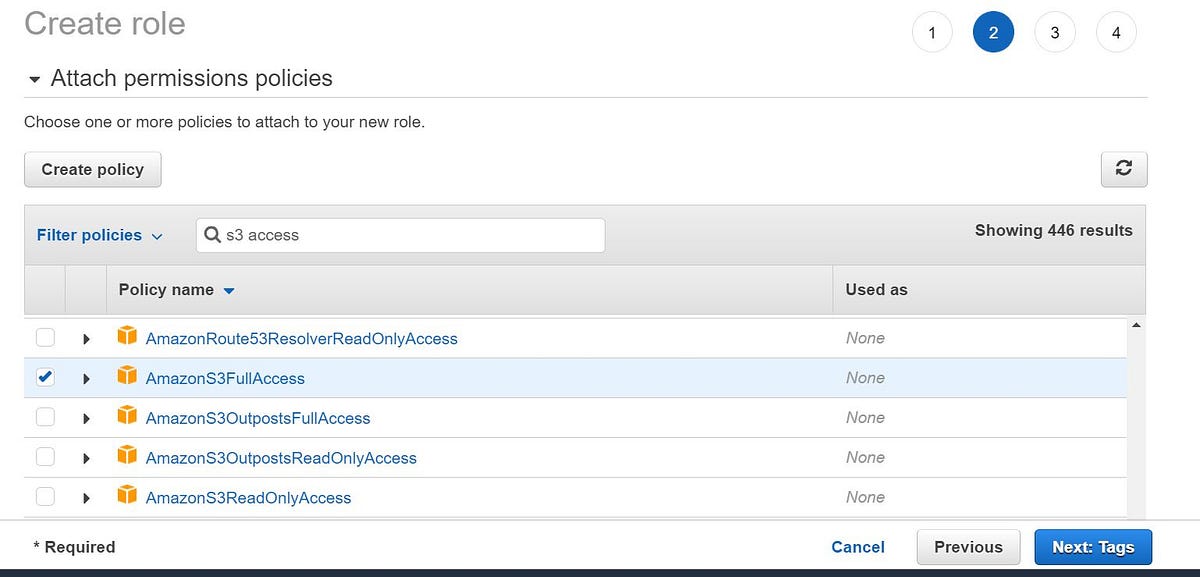
2. Click on the Next: Permissions option after which you will be asked to select the permission policy (here we need S3 full access) and select AmazonS3FullAccess. Click on Next: Tags and give any naming tags if you wish to.
3. Give the relevant Role name and click on Create role and now your role is ready to attach to an EC2 instance. You can find your Role under the Role name list once it is created.
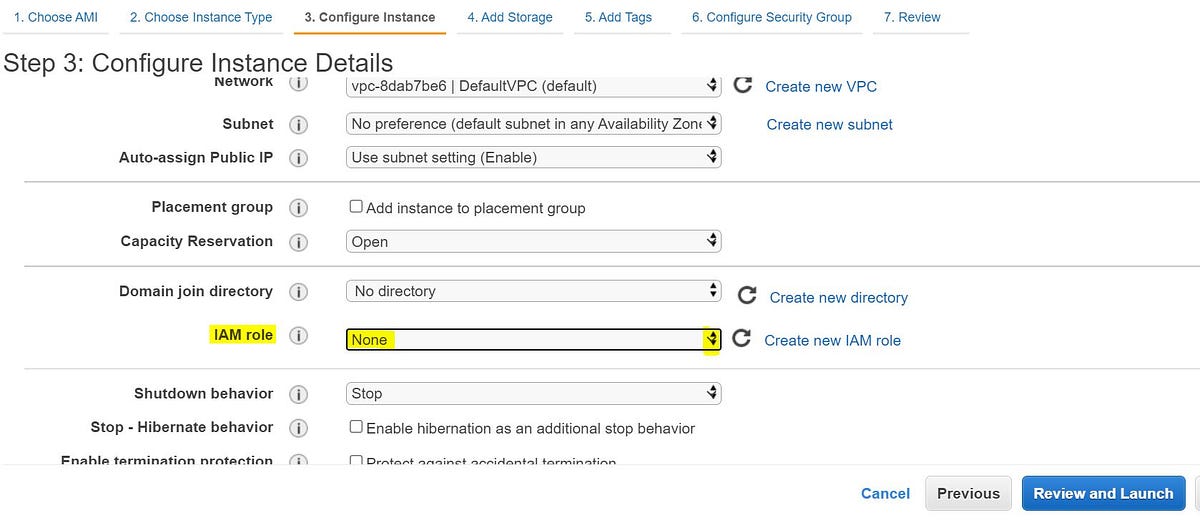
The second part is to attach the Role to the EC2 instance and verify:
- An IAM Role can be attached to an instance at the time of launching it or even after launching it via Modify IAM Role under the EC2 Actions tab.
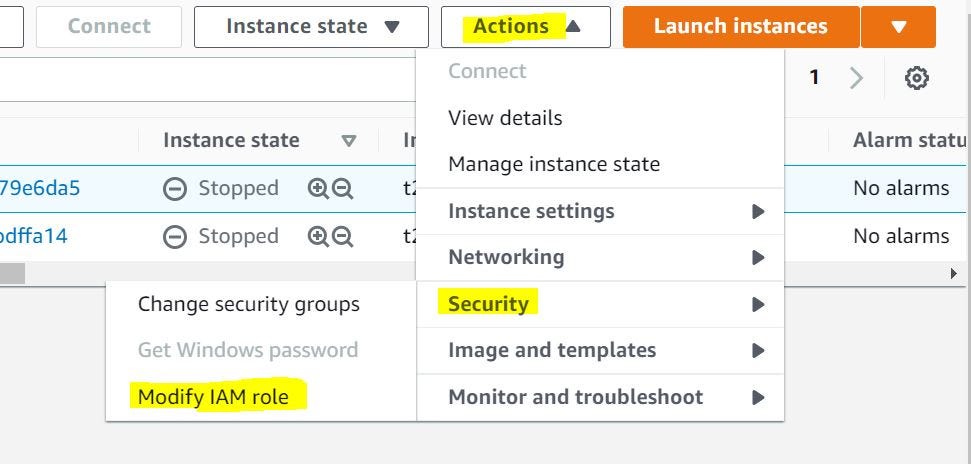
2. After attaching the required Role we can see in the below snip that the EC2 instance is able to make S3 calls without putting in any credentials.
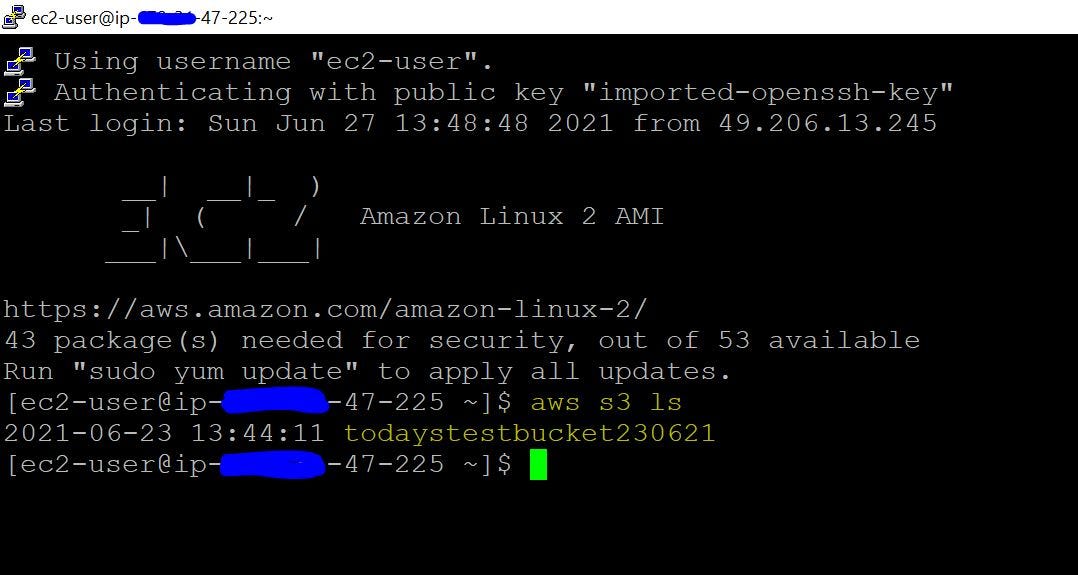
Like this, we can use IAM Roles to define a set of permissions for making AWS service request.
IAM Policies
After going through IAM Roles you must have now got little idea of what actually IAM Policies are.
IAM policies define permissions for action regardless of the method that you use to perform the operation.
Roles are set of permissions attached to IAM User or any AWS Service whereas Policies are the permission sets attached only to an IAM User.
By considering the above Role where we chose AWS S3 full access let’s look inside this policy and understand how it is defined.
IAM Policies are defined in JSON and consist of key items such as Effect, Action, and Resource. We can make use of prebuilt Policies or can define our own.
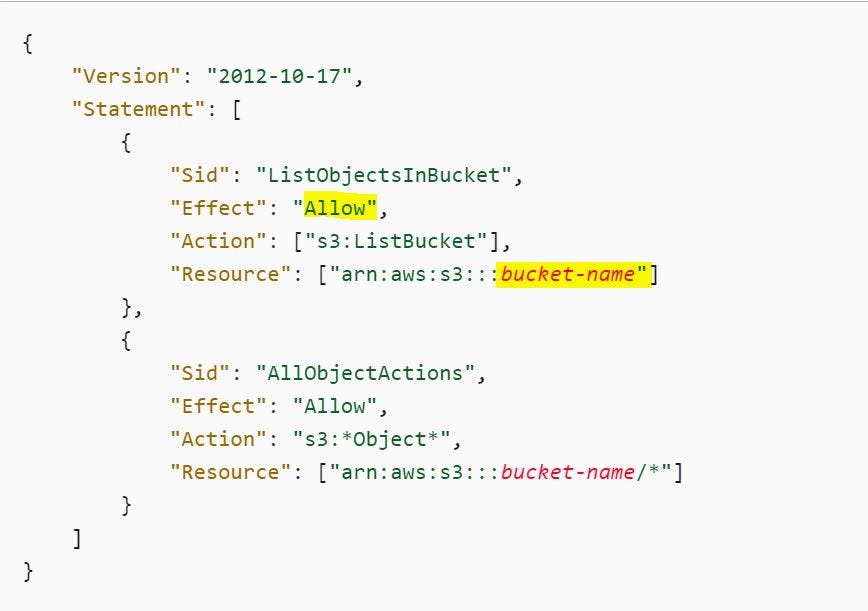
In the above policy, it has been given Allow effect to perform any kind of Action on the Resource S3 bucket.
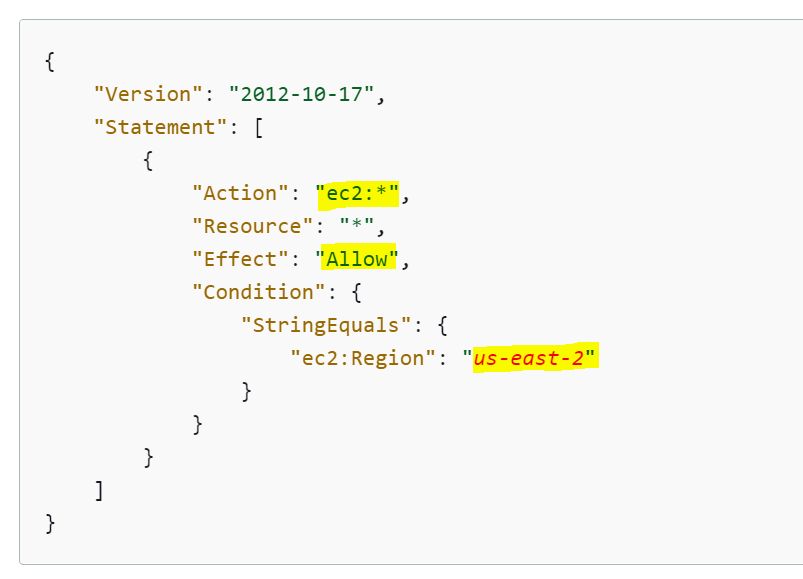
Let us take one more example policy below where an IAM User has only EC2 full access within a specific region. This user would not be able to perform any actions apart from EC2.
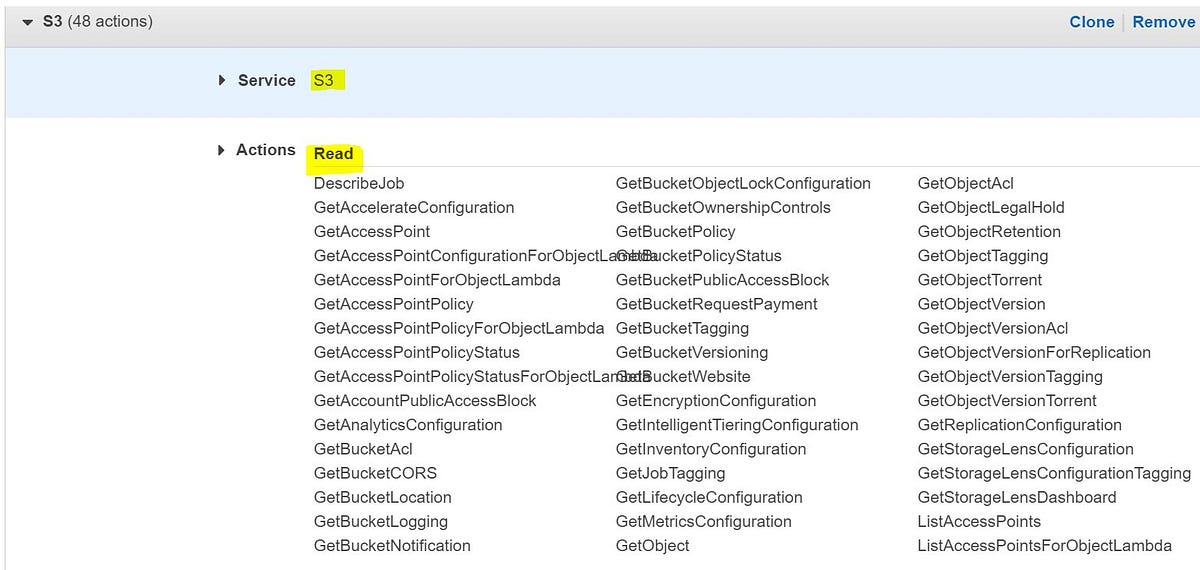
IAM Policies can also be defined manually by using Policy Generator as per the below steps:
- Under IAM go to Policies and select Create Policy.
- Will create a policy that provides S3 read-only access. Under service choose S3 and Actions is Read.
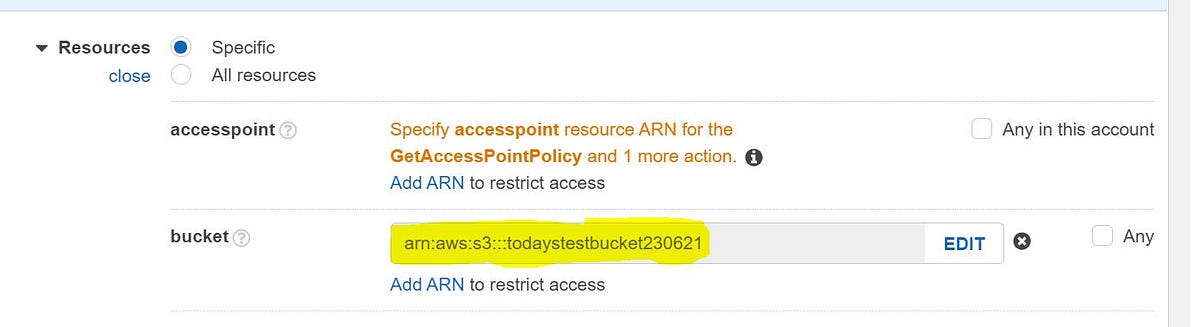
3. Under Resources choose specific points to which the access needs to be given. Once all required details are filled give a tag and create a Policy.
AWS IAM Switch Role
A role specifies a set of permissions that you can use to access AWS resources that you need. In that sense, it is similar to a user in AWS Identity and Access Management (IAM). … When you switch to a role, you temporarily give up your user permissions and work with the permissions that are assigned to the role.
Assume you are user A in an account XYZ having read-only access and now want to do some auditing in all other accounts and you need to switch to account B with read-only access. This can be achieved by performing Swith Role and in order to get this worked account id of A should be given permission in account B and account, A should be attached with STS (Security Token Service) permission.
FAQ’s
Q: What kinds of security credentials can IAM users have?
IAM users can have any combination of credentials that AWS supports, such as an AWS access key, X.509 certificate, SSH key, password for web app logins, or an MFA device. This allows users to interact with AWS in any manner that makes sense for them. An employee might have both an AWS access key and a password; a software system might have only an AWS access key to make programmatic calls; IAM users might have a private SSH key to access AWS CodeCommit repositories, and an outside contractor might have only an X.509 certificate to use the EC2 command-line interface. For details, see Temporary Security Credentials in the IAM documentation.
Q: Which AWS services support IAM users?
You can find the complete list of AWS services that support IAM users in the AWS Services That Work with IAM section of the IAM documentation. AWS plans to add support for other services over time.
Q: How do I assume an IAM role?
You assume an IAM role by calling the AWS Security Token Service (STS) AssumeRole APIs (in other words, AssumeRole, AssumeRoleWithWebIdentity, and AssumeRoleWithSAML). These APIs return a set of temporary security credentials that applications can then use to sign requests to AWS service APIs.
Refer to more FAQ’s at https://aws.amazon.com/iam/faqs/
“Learn and be curious”….. AWS is AWESOME!!!. Happy LEARNING!!!